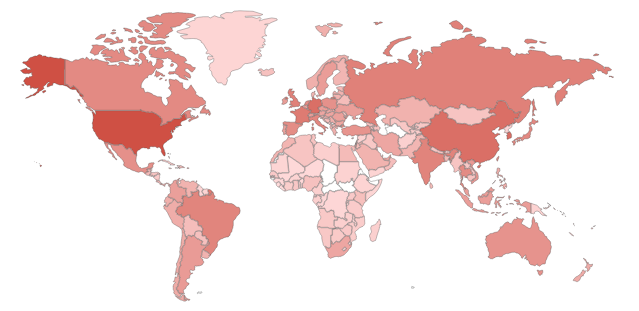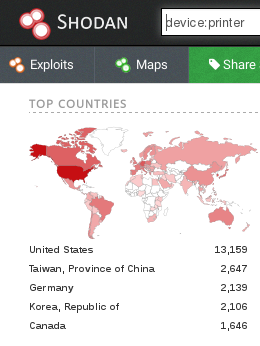
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
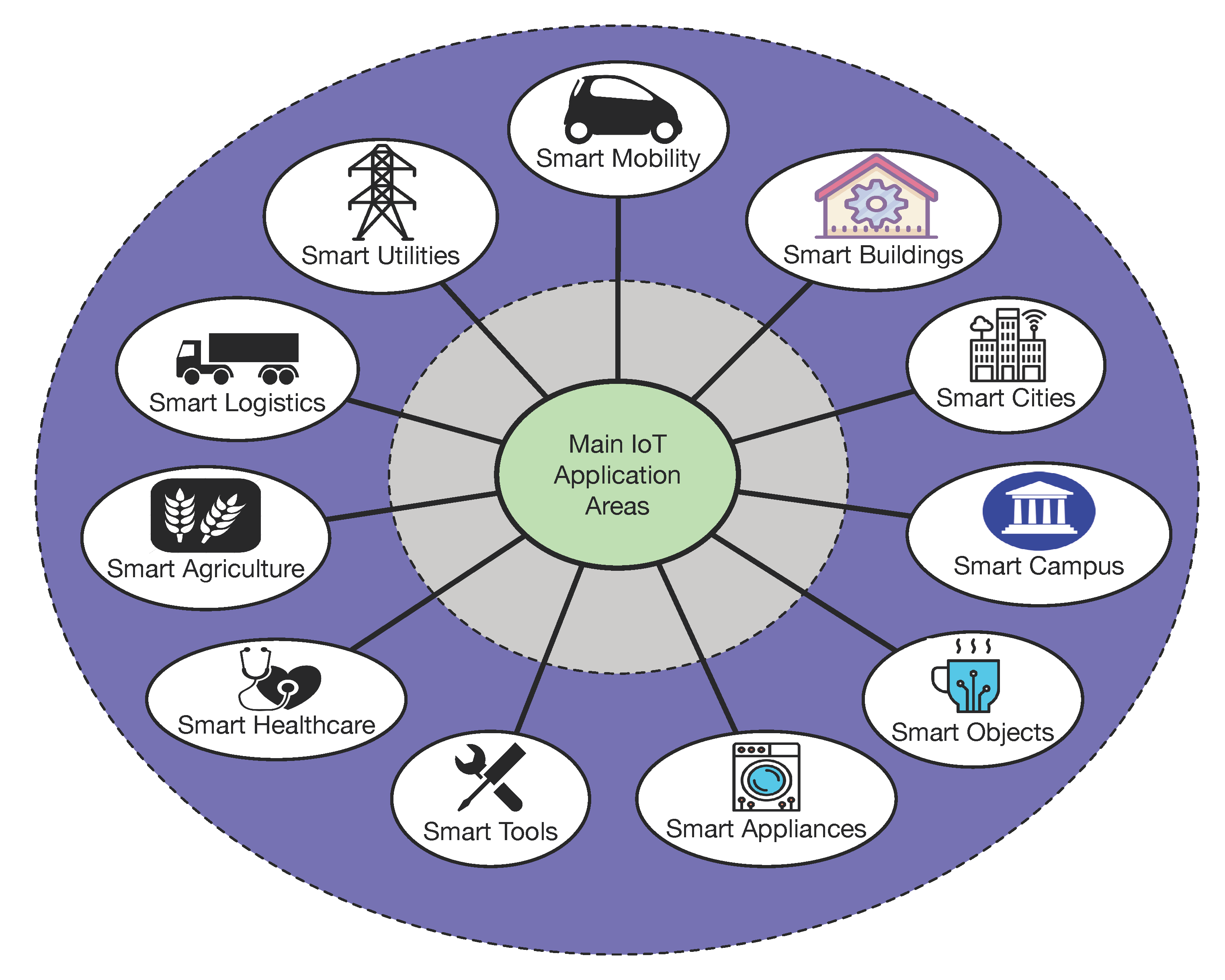
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
Applied Sciences | Free Full-Text | Use Case Based Blended Teaching of IIoT Cybersecurity in the Industry 4.0 Era

Shodan on Twitter: "Good news: Telnet use is in steady decline - https://t.co/8IsuWEDS1m https://t.co/FFxvt7RyJv" / Twitter